Saturday, January 30, 2010
Wmap trace.axd module
"Requests to this Application" inurl:trace.axd
OK. Now that this was explained I developed a small metasploit/wmap module that will look for trace.axd files available on an specific file and print sensitive information on the msfconsole. Obviously I took as a template other module and started from there.
The following is an example of how to use this module:
=[ metasploit v3.3.4-dev [core:3.3 api:1.0]
+ -- --=[ 320 exploits - 99 auxiliary
+ -- --=[ 217 payloads - 20 encoders - 6 nops
=[ svn r8140 updated 14 days ago (2010.01.16)
msf > use auxiliary/scanner/http/trace_axd
msf auxiliary(trace_axd) > show options
Module options:
Name Current Setting Required Description
---- --------------- -------- -----------
PATH / yes The test path to find trace.axd file
Proxies no Use a proxy chain
RHOSTS yes The target address range or CIDR identifier
RPORT 80 yes The target port
THREADS 1 yes The number of concurrent threads
VHOST no HTTP server virtual host
msf auxiliary(trace_axd) > set RHOSTS example.com
RHOSTS => example.com
msf auxiliary(trace_axd) > set PATH /path/
PATH => /path/
msf auxiliary(trace_axd) > run
.
.
.
http(s)://host_ip/path/Trace.axd?id=1
[*] User ID: user_id
[*] Password: pass
[*] Physical Path: \Inetpub\wwwroot\lalala
[*] Session ID: sgwz55xnci4145ahzbas
[*] Local Address: 10.168.10.180
[*] Headers: HEADERS
[*]
Again, I hope this helps someone. If you want to run this module along with the other wmap modules please look at the crawler post in this same blog or wmap documentation. Basically you just have to browse using a proxy and load the db_wmap module.
c4an.
Monday, January 25, 2010
VoIP basic discovery - VLAN hopping and TFTP
1. Connect your laptop to an IP phone.
2. Start Wireshark
3. Listen to traffic and wait until you capture a CDP package.
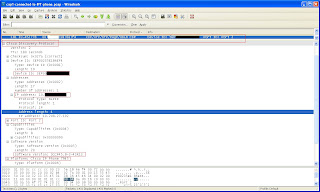
4. Connect to the http interface of the phone and review the VLAN number

5. Using voiphopper run the following command using the information discovered on the CDP packet and the phone HTTP interface.
./sudo voiphopper -i eth0 -v VLAN# -E DEVICE_NAME -P PORT_ID -C HOST -L DEVICICE_ID -S SOFTWARE_VERSION
It is really important that you know that when you do VLAN hopping you usually can bypass network restrictions that you will usually have connected to a user network, this can be really helpful in any kind of pentest and not only when testing VOIP.
This is a good link that explains the basics of VLAN hopping:
http://www.securityfocus.com/infocus/1892
4. Run nmap to identify the services that are available on your network. It is important that you also identify servers to which the telephones are reporting such as TFTP server.
5. When you identify the TFTP server a good way to learn more about the IP telephony infrastructure you can do the following: Using tftpbrute or a simple TFTP client try different file to download from the TFTP server.
./tftpbrute.pl IP_ADDRESS brutefile.txt 100
List of files that might work:
fsck.fd0a.log
fsck.fd1a.log
jar45sccp.8-3-3-17.sbn
Ringlist.xml
DEVICE_NAME.cnf.xml
term45.default.loads
Test that the TFTP server is well configured and that you cannot upload any random file to it. Please keep in mind whenever you are uploading files to the TFTP server that all IP phones will take this files as configuration files so you can really screw the hole VoIP infrastructure if you are not careful.
c4an.
Exploit writing tutorial! (link to a great blog)
You will find links to the other tutorials at the end of each article.
Sunday, January 24, 2010
Metasploit: msfproxy, crawler and wmap
This is my first version of a ruby simple crawler. The main idea of this tool is to use it while interacting with the wmap database and populate the request table. Because this is my first version the database interaction is not as clean as I would like but I still believe it can be used. Now, I know for a fact that ET (creator of wmap) is already working on a crawler of its own with a lot of modularity and cleaner options. However since I already had this code with me I thought that it was a good idea to post it. Who knows maybe it will help someone :)
Things that you have to know before you start using this crawler is that it uses hpricot as its primary library. If hpricot is not installed it will use a function that I developed. Hpricot can be installed on ruby by typing:
sudo gem install hpricot
The first thing that you have to do is download the code and save it into the mf3/tools/ .
Now, there are two options to run the crawler and then being able to run wmap modules based on your discovery:
OPTION 1. Two consoles (you can any crawler with this option)
1. Open two separate consoles and go in both of them to the mf3/tools/ folder.
2. On the first console open a metasploit msfconsole and follow the steps bellow:
| | _) |
__ `__ \ _ \ __| _` | __| __ \ | _ \ | __|
| | | __/ | ( |\__ \ | | | ( | | |
_| _| _|\___|\__|\__,_|____/ .__/ _|\___/ _|\__|
_|
=[ metasploit v3.3.4-dev [core:3.3 api:1.0]
+ -- --=[ 320 exploits - 99 auxiliary
+ -- --=[ 217 payloads - 20 encoders - 6 nops
=[ svn r8140 updated 8 days ago (2010.01.16)
msf > cd tools
msf > db_driver sqlite3
[*] Using database driver sqlite3
msf > db_create wm_req.db
[*] Creating a new database instance...
[*] Successfully connected to the database
[*] File: wm_req.db
msf > load db_wmap
[*] =[ WMAP v0.6 - et [ ] metasploit.com
[*] Successfully loaded plugin: db_wmap
msf > db_connect wm_req.db
[*] Successfully connected to the database
[*] File: wm_req.db
msf > ruby msfproxy.rb -w wm_req.db
3. On the second console run the following command:
ruby crawler.rb -h
Usage: crawler.rb
OPTIONS:
-a Print website structure
-c Create database to interact with wmap
-h Display this help information
-i
-j
-l Log visited websites in a text file /msf3/tools/crawler.log
-m Add discovered links to wmap database as targets. Options: -c or -w required
-n Print new possible targets during crawling
-p
-v Verbose
-w
ruby crawler.rb -i 127.0.0.1 -p 8080 -v -j 1 -t http://www.target.com/
4. After the crawler ends return to the metasploit console, stop the msfproxy and type the following
msf > wmap_targets -r
msf > wmap_run -e
OPTION 2. One console
____________
<>
------------
\ ,__,
\ (oo)____
(__) )\
||--|| *
=[ metasploit v3.3.2-release [core:3.3 api:1.0]
+ -- --=[ 463 exploits - 218 auxiliary
+ -- --=[ 192 payloads - 22 encoders - 8 nops
=[ svn r7808 updated 40 days ago (2009.12.10)
Warning: This copy of the Metasploit Framework was last updated 40 days ago.
We recommend that you update the framework at least every other day.
For information on updating your copy of Metasploit, please see:
http://dev.metasploit.com/redmine/projects/framework/wiki/Updating
msf > cd tools
msf > db_driver sqlite3
[*] Using database driver sqlite3
msf > db_create wm_req.db
[*] Creating a new database instance...
[*] Successfully connected to the database
[*] File: wm_req.db
msf > load db_wmap
[*] =[ WMAP v0.6 - et [ ] metasploit.com
[*] Successfully loaded plugin: db_wmap
msf > db_connect wm_req.db
[*] Successfully connected to the database
[*] File: wm_req.db
msf > ruby crawler.rb -v -j 1 -w wm_req.db -t http://www.target.com/
.
.
.
msf > wmap_targets -r
msf > wmap_run -e
Hope this helps someone.
Thanks
c4an.